Europe's online source of news, data & analysis for professionals involved in packaged media and new delivery technologies

Sizing piracy - 24% total bandwidth used to access illegal content
NetNames has produced a study that provides an estimate of the shape and size of the piracy universe. Absolute infringing bandwidth use increased by 159.3% between 2010 and 2012, from 3,690 petabytes to 9,567 petabytes (1petabyte = 1 million gigabytes). This figure represents 23.8% of the total bandwidth used by all internet users, residential and commercial, in these three regions.
The 100-page report, commissioned by NBCUniversal and prepared by the Piracy Analysis team at NetNames, is based on in-depth research of a range of ecosystems commonly used for the distribution of infringing content. The study demonstrates the number of unique internet users who employ each infringement method to obtain material as well as the overall proportion of internet bandwidth used by each ecosystem for infringement.
The bottom line: Internet usage continues to grow at a rapid pace; and with it, so does internet-based infringement. The practise of infringement is tenacious and persistent. Despite some discrete instances of success in limiting infringement, the piracy universe not only persists in attracting more users year on year but hungrily consumes increasing amounts of bandwidth.
The free and simple availability of copyrighted content through piracy ecosystems continues to drive the popularity of hundreds of web sites, the actions of hundreds of millions of internet users worldwide, and the consumption of thousands of petabytes of internet bandwidth.
Users of piracy ecosystems, the number of internet users who regularly obtain infringing content, and the amount of bandwidth consumed by infringing uses of content all increased significantly between 2010 and 2013.
Three key regions - North America, Europe, and Asia-Pacific - make up a majority of the internet world, comprising 82.6% of all internet users and 95.1% of all bandwidth consumed.
Some 327 million unique internet users explicitly sought infringing content during January 2013. This figure increased by 9.9% in the fifteen months from November 2011 and represents 25.9% of the total internet user population in these three regions (i.e., 1.26 billion internet users).
13.9 billion page views were recorded on web sites focused on piracy in January 2013. This figure increased by 9.8% in the fifteen months from November 2011.
Worldwide, 432 million unique internet users explicitly sought infringing content during January 2013.
Infringement ecosystems
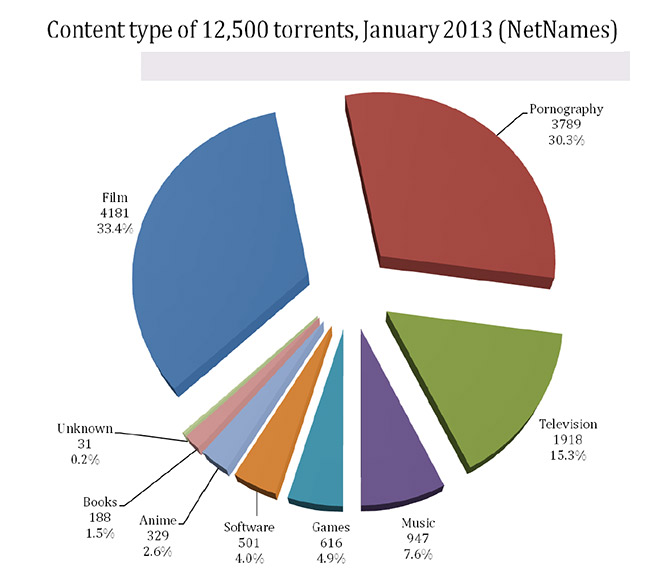
Bittorrent is the most popular peer-to-peer file distribution system worldwide and the protocol is one of the highest consumers of internet bandwidth. In three key regions (North America, Europe, and Asia-Pacific), the absolute amount of bandwidth consumed by the infringing use of bittorrent comprised 6,692 petabytes of data in 2012, an increase of 244.9% from 2010.
In the same three regions, infringing use of bittorrent in January 2013 accounted for 178.7 million unique internet users, an increase of 23.6% from November 2011, and 7.4 billion page views, an increase of 30.6% from November 2011.
Infringement through video streaming generally combines video streaming link sites with video hosting sites that are often called video streaming cyberlockers. In three key regions (North America, Europe, and Asia-Pacific), the absolute amount of bandwidth consumed by the infringing use of video streaming comprised 1,527 petabytes of data in 2012, an increase of 471.9% from 2010.
In the same three regions, infringing use of video streaming in January 2013 accounted for 96.3 million unique internet users, an increase of 27.7% from November 2011, and 4.2 billion page views, an increase of 34.3% from November 2011.
Levels of infringement on direct download cyberlockers were affected by the seizure of the MegaUpload site in January 2012 and the subsequent closure of other popular direct download cyberlockers. In three key regions (North America, Europe, and Asia-Pacific), the absolute amount of bandwidth consumed by the infringing use of direct download cyberlockers comprised 338 petabytes of data in 2012, a decrease of 54.7% from 2010.
In the same three regions, infringing use of direct download cyberlockers in January 2013 accounted for 148.6 million unique internet users, a decrease of 7.7% from November 2011, and 2.3 billion page views, a decrease of 40.6% from November 2011.
Almost every piracy-focused site used as the basis of analysis in the report is owned and run for profit. Business models differ slightly within the different ecosystems discussed, but the majority of these sites draw revenue from advertising, with others supplementing this income by offering users premium subscription accounts designed to offer faster access to content.
Distribution and enforcement
Efforts to restrict infringement through legal action or other methods have been only intermittently successful, limited by the abilities of those involved to use available processes and techniques to adequately tackle the complexities of the internet world and the adaptive nature of infringement, the latter driven by a voracious online appetite for pirated content.
The rise in the number of users involved in infringement, the page views devoted to piracy, and the amount of bandwidth consumed by infringement comes despite the discrete success stemming from the law enforcement operation against the MegaUpload direct download cyberlocker in January 2012 that limited the attractiveness and use of direct download cyberlockers.
The closure of MegaUpload also involved the closure of the major video streaming cyberlocker MegaVideo. This disruption did not have a similar permanent impact on infringing use of video streaming as for the direct download cyberlocker ecosystem. Video streaming, both as a legitimate and illegitimate practice, is simple to engage with and deeply embedded in typical user routine. Infringement through video streaming increased dramatically in the period studied in the report.
Online piracy reacts quickly to system events such as site closures or seizures. User behaviour is modified, often in moments, shifting from locations or arenas impacted by events to others that offer a comparable spread of infringing content via a similar or different consumption model. The practise of piracy morphs to altered circumstances: as direct download cyberlockers fell in popularity, use of video streaming and bittorrent escalated.
The value to content owners of the international law enforcement action against MegaUpload and the effect on the overall direct download cyberlocker ecosystem is undeniable. The recovery of infringing video streaming from the same incident and the overall growth in infringing users, page views, and bandwidth consumption in the infringing video streaming ecosystem demonstrates a need for content owners to have access to tools and methods that allow them to react no less quickly as users and site operators do to changes and transformations in the different piracy ecosystems.
Research Methodology
The research provided in the report presents what is believed to be the first attempt to produce an accurate overall size estimate for the online piracy universe. Estimating any activity that comprises a range of user behaviours, motives, and actions can be problematic and is inevitably open to criticism and question. By carefully outlining in the body of the report the methodologies used to produce the conclusions, it is hoped that the research might prompt further study in one of the most fascinating and consistently changing areas of the internet.
The research draws on data from a number of sources. In all cases, data from external sources was used to strengthen and augment original research conducted by NetNames. The selection of sites which comprise the different ecosystems studied in the report are based on the company's experience, knowledge, and monitoring of digital piracy for more than fourteen years. In all ecosystems studied in the report, a careful account has been made of levels of non-infringing use. Using various techniques devised by NetNames, each explained in detail within the report, the research examines the types of content available within each ecosystem and the proportion of that content which is infringing.
Story filed 25.09.13




















